Introduction
The Virtual Signer is a server-side Multi-Party Computation (MPC) program integrated with io.vault and io.network. It implements trustless MPC to create and manage vaults, sign transactions, and perform other operations involving threshold digital signatures on the io.finnet platform.
One running instance of the Virtual Signer application may control one or more virtual devices in an io.vault organization. Vaults may contain a combination of virtual or mobile devices. Communicating together, these devices carry out vault operations: the creation
of vaults, the reconfiguration of vaults and the creation of transaction signatures.
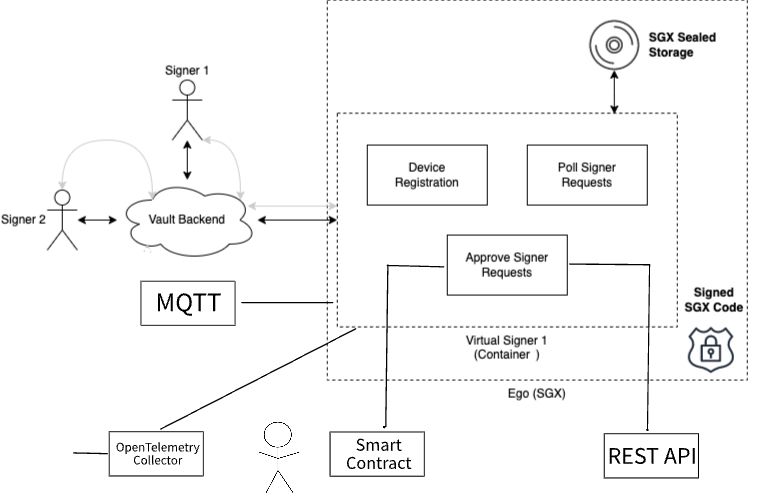
Virtual Signer uses Intel® SGX technology for encrypted storage and execution
The Virtual Signer runs in a Intel Software Guard Extensions (SGX) secure enclave. SGX enclaves are hardened environments where the application code,
its memory and data are inaccessible outside the enclave. In order to perform TSS operations, the Virtual Signer reads and writes sensible data, including private keys and private shares, but data is encrypted at all times - both during runtime and at rest.
For more information on Intel SGX see What Is Intel® SGX? and Azure confidential computing - SGX enclaves.
Transaction Flow
Let us consider 3 operations of the Virtual Signer: key generation, resharing and signing.
In each operation, the Virtual Signer queries a backend – known as GraphQL – to fetch requests waiting for approval. The Virtual Signer, in turn, forwards each request to an external application (external API or io.network Smart Contract) for approval or rejection.
A successful reply is considered an approval vote.
Once quorum is formed by collecting enough approvals, the io.vault makes the operation available to the Virtual Signer. The operation is performed by multiple parties, which may be a combination of Virtual Signer devices and/or mobile devices. All of these devices must have approvals locally registered through either the API approver, Smart Contract or human biometric verification via the io.vault apps.
For example, an io.network transaction may be approved by one or more Virtual Signers, or it may rely entirely on manual approvals from mobile devices. The requirements for a vault depend on the vault's configuration, managed through vault.iofinnet.com.
The Virtual Signer retrieves the corresponding transaction request, participates in MPC-TSS with the approved devices to generate a signature for the transaction, and sends it to the backend, which broadcasts the signed transaction to the target blockchain.
Prerequisites
This is what you will need to get up and running with a Virtual Signer linked to your io.vault.
- A server that meets the minimum or recommended requirements below.
- Firewalls and other appropriate security measures enabled.
- An API key created from your io.vault dashboard to be entered into the environment variables settings of the Virtual Signer.
- A web hook set up in your backend infrastructure to handle incoming approval request calls from the Virtual Signer, or a smart contract that handles approvals. See the Approvals in API mode and Approvals via Smart Contracts sections for more information.
Your machine should be appropriately hardened (disk encryption turned on, SSH keys required, no root login, etc.), and meet the following requirements:
Minimal Requirements
- Linux OS. Ubuntu 22.04 LTS or greater with the latest security updates applied
- Docker version 20.10+
- 4GB RAM+ with swap
- Intel Xeon CPU with SGX support (check here)
- 20 GB+ SSD storage
- Latest Intel micro-code (BIOS update). This is automatically applied on Microsoft Azure.
On Azure, we have tested a minimal system with Standard_DC1s_v2 instances on a DCsv2-Type1 Dedicated Host.
This host type is able to run 6 isolated virtual signers, each in their own Standard_DC1s_v2 VM instance.
This offers great security, as it means that your signers will run within several layers of defense (SGX, the Docker container, the VM itself and the Dedicated Host).
Recommended Requirements for High-Throughput
- Linux OS. Ubuntu 22.04 LTS or greater with the latest security updates applied
- Docker version 20.10+
- 8GB RAM+ with swap
- 8-core+ Intel Xeon CPU with SGX support, such as Intel Xeon E-2288G (check here)
- 20 GB+ SSD storage
- Latest Intel micro-code (BIOS update). This is automatically applied on Microsoft Azure.
On Azure, we have tested a recommended system with a Standard_DC2s_v2 instance on a DCsv2-Type1 Dedicated Host.
This host type is able to host 3 isolated virtual signers, each in their own Standard_DC2s_v2 VM instance.
As with the minimal requirements above, it's best not to share VM instances for security reasons. If you would like to, it's possible to host several Virtual Signers on one VM instance and share its resources.
Networking Requirements
You may deploy a firewall to enable outbound access only to the following trusted and TLS-enabled endpoints.
mqtt.vault.iofinnet.com, port8084, TCPapi.iofinnet.com, port443, TCP- Host and port defined by
ExternalReshareApprovalURLin configuration ifApprovalModeis "API", TCP - Host and port defined by
ExternalTransactionApprovalURLin configuration ifApprovalModeis "API", TCP - Host and port defined by
ApprovalNodeRPCAddressin configuration ifApprovalModeis "SmartContract", TCP - Host and port defined by
OTELExporterOTLPEndpointin configuration ifTraceSpanExporterisOTLP-NO-TLSorOTLP-TLS, TCP - Host and port defined by the
OTEL_EXPORTER_OTLP_LOGS_ENDPOINTenvironment variable ifTraceSpanExporterisOTLP-NO-TLSorOTLP-TLS, TCP
For inbound access, enable the port defined by Port in configuration, TCP. That is only required if new Virtual Signer
devices besides the initial one will be registered using the Virtual Signer API.
Approval Modes
The Virtual Signer supports several Policy Modes when processing transactions. We recommend using the Virtual Signer App to set up and configure the various modes of approval according to your needs.
Further Information
For more information on the Virtual Signer and setup steps & requirements, contact your sales representative and ask for a copy of the Virtual Signer Implementation Guide PDF.
Updated 3 months ago